Authors : Sh. Bhargav Nerayanoor ; Sh. Gaurav Jagadeesh
MMS: A Protocol that Refuses to retire
Manufacturing Message Specification (MMS), standardized as ISO 9506, its latest published version is from 2003. It continues to serve as the primary client–server communication protocol for IEC 61850-based substation automation systems. This temporal disconnects between a frozen communication core, and an increasingly interconnected, software-driven substation environment underpins many of the architectural, operational, and integration challenges observed today.
IEC 61850 successfully established a standardized data model and abstract service interface through the Abstract Communication Service Interface (ACSI), enabling interoperability and vendor-neutral engineering across substations. MMS was selected as the concrete mapping for these services based on assumptions of closed, trusted networks and static system boundaries. While this pairing was effective for early automation objectives, the surrounding operational context has changed fundamentally.
Rather than evolving the MMS protocol itself, the industry has responded through compensating mechanisms: security overlays, integration gateways, architectural containment, and specialized tooling. These measures preserve backward compatibility, but at the cost of increasing complexity and operational friction. This pattern reflects a systemic deadlock in which MMS persists not because it is actively chosen, but because it is difficult to displace.
The challenges discussed here are not isolated deficiencies, nor are they solely cybersecurity concerns. They are the cumulative effects of operating modern substation automation systems atop a communication model whose core assumptions no longer align with the realities of contemporary power system infrastructure.
The Core Fact
First published in 1990, standardising the messaging system for transferring real time process data and supervisory control information between network devices or computer applications. It defined the following,
- A set of standard objects which must exist in every device, on which operations like read, write, event signalling etc. can be executed. Virtual manufacturing device (VMD) is the main object and all other objects like variables, domains, journals, files etc. comes under VMD.
- A set of standard messages exchanged between a client and a server station for the purpose of monitoring or controlling these objects.
- A set of encoding rules for mapping these messages to bits and bytes when transmitted.
It was standardised under two standards in 1990
- ISO/IEC 9506-1: Industrial Automation systems – Manufacturing Message Specification – Part 1: Service Definition
- ISO/IEC 9506-2: Industrial Automation systems – Manufacturing Message Specification – Part 2: Protocol Specification

The latest version is version 2 and was last published in August 2003, roughly 22 years ago. Thus, MMS has not meaningfully evolved since 2003. Everything that follows is a consequence of this fact.
Aspect | MMS Reality | Modern Substation Reality |
| Evolution pace | Frozen | Continuous |
| Design assumptions | Closed, trusted | Connected, segmented |
| Change tolerance | Low | High |
| Integration model | Protocol-centric | Service-centric |
| Security posture | Add-on | Intrinsic |
Why MMS Still Exists?
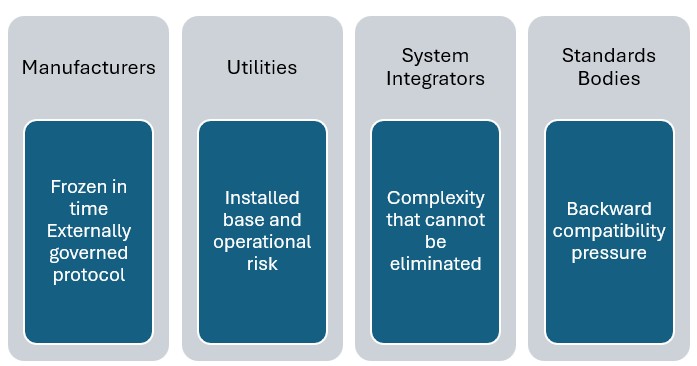
Originally selected for being the best technical choice of what was available at the time, now is effectively mandated for compliance within the standard. Thus, MMS persists in the power utility system.
For compliance manufacturers implement MMS to comply with IEC 61850. Utilities deploy MMS because it is already installed. System integrators design around MMS because it cannot be replaced in isolation. Standards bodies extend around MMS to avoid breaking compatibility.
This is a classic case of technological lock-in.
Note: Technological lock-in is the idea that, as economic and cultural advantages accrue to existing incumbent technologies, barriers are created to the adoption of potentially superior or at least as valuable alternatives. This occurs because technological innovation and deployment are path dependent and take place under conditions of uncertainty. Technologies coevolve with supporting institutions, business strategies, and user practices; and individuals, firms, and governments are subject to bounded rationality.
No stakeholder is incentivized to change the core. Every stakeholder is incentivized to tolerate it.
What This Causes in Real Systems??
The effects of a frozen communication core appear not as failures, but as friction.
Architecture Grows Sideways
When MMS cannot adapt, it aids to the architectural technical debt of the overall system-architecture and forces the system-architecture to absorb the difference. The absorption would be through mandatory wrappers, gateways, concentrators, and translators appear.
These remain persistent in the system. Thus, Complexity becomes structural.
Security Is Built Around the Protocol
Security for IEC 61850 remains an externalized overlay because MMS lacks the native vocabulary to express modern security intent. Since the protocol cannot verify identity or encrypt its own data, the architecture must absorb these risks through peripheral defences like firewalls, data diodes, and IEC 62351 wrappers. This creates a brittle dependency where security is not inherent to the communication itself but is instead a fragile perimeter that only functions if every external “shield” remains perfectly operational. Security works when everything else works.
| Year | Security Strategy | The Role of MMS |
| 2004 | Isolation | Assumed safe because it was on a private, air-gapped network. |
| 2015 | Perimeter | Shielded by firewalls; security intent handled at the “gate.” |
| 2025 | Zero Trust Overlay | MMS remains unchanged but is wrapped in TLS 1.2/1.3 and IEC 62351 certificates. |
Integration Becomes Translation
With modern power utility system requiring observability, automation, fine-grained access, enterprise integration. In line with the technical debt, to compensate the system bears the burden of translation in the name of integration. MMS is rarely integrated directly. It is translated. Each translation adding a bridge that adds a new piece of hardware to maintain, a new point of failure and a permanent source of data delay. In short, the integration becomes a permanent overhead.
| Requirement | What MMS Lacks | What Gets Added |
| Fine-grained access | Intent-level control | Firewalls, ACLs |
| Enterprise integration | Native interfaces | Gateways |
| Observability | Inspectable semantics | Protocol analysers |
| Automation | Lifecycle hooks | Manual workflows |
Engineering Remains Manual
The engineering of digital substations remains a fundamentally manual, risk-averse process. Configuration changes rely heavily on proprietary vendor tools due to limited true interoperability within the IEC 61850 standard. The high risk associated with automated rollbacks is prohibitive, leading utilities to favour cautious, manual deployment strategies over modern IT automation techniques. Consequently, significant engineering effort is expended merely to manage the rising complexity of the grid, without delivering a corresponding increase in operational agility.
Observability Is Limited
Observability in digital substations is severely restricted by the nature of the communication itself. Because MMS traffic is ASN.1-encoded and increasingly shielded by external encryption layers, standard network tools cannot easily inspect the data. This lack of transparency means that troubleshooting depends entirely on a small pool of specialists who understand these specific protocols. Consequently, identifying the root cause of an issue becomes a bottleneck, making system resolution significantly slower and more complex than modern digital standards require.
Expertise Concentrates
The power system infrastructure outlives the engineers who design it. MMS knowledge is shrinking as its specialized complexity fails to attract new talent, leaving a dwindling pool of experts to manage the world’s most critical systems. This creates a dangerous divergence where the grid’s lifespan exceeds the career span of its specialists, forcing utilities to rely on legacy logic they no longer fully understand. Consequently, technical and operational risk accumulates quietly behind the scenes, as the ability to troubleshoot and secure these systems vanishes while the hardware itself remains in service for decades.
Innovation Avoids the Core
MMS has transitioned from a living technology to an immutable foundation. Becoming an example of protocol ossification, being treated like a black box where no one touches it or risks breaking it. And innovating the system means to route around this black box. Through out the years the core MMS remains untouched, a rigid and permanent foundation that dictates architecture of modern grid will all evolution happens externally.
| Layer | Innovation Level |
| MMS protocol | None |
| Data models | Active |
| Security overlays | Active |
| Middleware / gateways | Very active |
| Monitoring / analytics | Very active |
What Changes When MMS Is Not the Bottleneck
When the core communication protocol is unfrozen and allowed to evolve, the entire system architecture transforms from the compensatory model seen with MMS to a more efficient, agile structure. Architecture grows linearly as new functionalities are integrated directly into the communication core, rather than being shunted to external layers. Security transitions from a brittle perimeter-based overlay to a native, in-band feature of the protocol itself. This fundamentally decreases the integration effort, as functionality can be reused across the enterprise without constant translation. Consequently, engineering processes become highly automatable, moving away from manual workflows, and observability becomes a routine, built-in feature of the system. The expertise required broadens beyond niche specialists to general IT practices, ultimately allowing innovation to simplify the overall system architecture rather than complicating it with layers of workarounds
| Dimension | MMS-Centric | Non-Frozen Core |
| Architecture growth | Sideways | Linear |
| Security effort | Compensatory | Native |
| Integration trend | Increasing cost | Decreasing cost |
| Engineering | Manual | Automated |
| Troubleshooting | Specialist-driven | Routine |
Uncomfortable Truth
The uncomfortable truth to digest is that MMS is not failing technically, but rather economically and structurally. While it remains operationally stable, its rigidity forces a reliance on a constant stream of workarounds to meet modern requirements. Each of these fixes , whether a new security layer or, a translation gateway adds immediate cost and structural complexity without reducing the effort required for future innovation. The result is a system where the cost of maintenance grows exponentially, yet the architecture remains fundamentally stagnant, trapped in a cycle where every “solution” only increases the burden of technical debt.
| Intended Outcome | Actual Result |
| Interoperability | Adapter sprawl |
| Standardization | Vendor-specific tooling |
| Security | Layered complexity |
| Reliability | Fragile configurations |
| Futureproofing | Deferred decisions |
Closing Thought
MMS enabled a generation of substation automation, effectively solving the problems of its era. However, protocols are not immortal. When the core of a system remains static while the environment around it evolves, complexity, cost, and risk inevitably migrate outward into the surrounding architecture. Recognizing this condition is not an indictment of sound decisions made in the past; it is a critical prerequisite for making conscious, forward-looking choices today.
Citations
- Manufacturing Message Specification
- Technological lock-in – Foxon, T.J.. (2013). Technological Lock-In. 10.1016/B978-0-12-375067-9.00067-X.
- Technical debt – IBM Insights
- Implementation Design and Performance Analysis of an IEC 61850 MMS Server – IEEE SmartGridcomm 2012
- Special Report IEC 61850 – (ABB review)The corporate technical journal

